Shortly after midnight on a Sunday – a well-known, non-peak hour for Twitter users – the junior senator from Texas launched his 2016 presidential bid with a 30-second YouTube video, “A Time for Truth.”
I'm running for President and I hope to earn your support! pic.twitter.com/0UTqaIoytP
— Ted Cruz (@tedcruz) March 23, 2015While a seemingly good enough start in this brave, new, online world of political campaign fundraising, it took no time at all and some sticky fingers while Googling “Ted Cruz” for the Internet to realize that tedcruz.org appears to be: 1) the one, and perhaps only, domain owned by Ted Cruz at this time, and 2) as secure as the domain of nigerian-prince.com.
Cannot make it up: @tedcruz' website *does* support SSL (just not default), – cert is also for nigerian-prince,com pic.twitter.com/bNk61WhnS1
— Pwn All The Things (@pwnallthethings) March 23, 2015Hat tip to @pwnallthethings for calling this fact out.
Aside from the fact that Team Cruz could have chosen a better name than “tedcruz” — perhaps a name that has NOT been owned since 2004 as a dot-com (tedcruz.com) or that is now being used to troll Cruz over his stance on immigration:

The more serious concern for Team Cruz to address is the question of online security. One big no-no in online fundraising is an un-secured donation page. As Vox illustrated, there was no padlock icon in the address bar of the donation page of tedcruz.org to indicate that the entire donation process online is SSL-protected 13 hours after the website had launched. (It was updated later in the day and fixed).
Here’s an example of a website with a padlock icon in the address bar:

Here’s a screenshot from the Ted Cruz for President donation page:
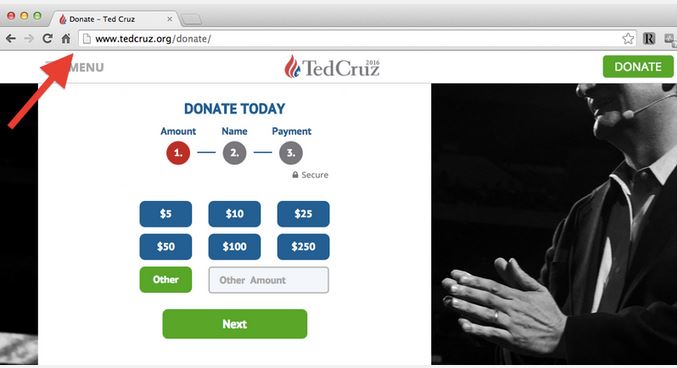
Although tedcruz.org is SSL-protected for anyone who navigates directly to the donation page, anyone who arrives at the donation page via another channel may encounter this message: “This page includes other resources which are not secure.” The idea that not everything in that donation page is encrypted is enough to make you rethink even hanging around the webpage for too long. Okay, not really, but it’s not a very comforting message to see right before you input your credit card information.
Someone donating via tedcruz.org is not SSL-protected from start to finish for that transaction. There is an opening for what cyber-security specialists call “man-in-the-middle attacks” (MITMA), in which an attacker is able to take advantage of a user by successfully impersonating one of the endpoints. In this case, all it would take is one attacker with the ability to impersonate tedcruz.org to then redirect a donating user to a malicious site instead.
Or in this case, a non-malicious, but still not-so-good for Ted Cruz redirect: http://TedCruzForAmerica.com
Ted Cruz doesn’t get his campaign donation. Some poor user is now a victim of credit card fraud.
If Ted Cruz is not even the master of his own domain name, how is he going to run a comprehensive, sophisticated online fundraising campaign?
As a digital native, I cannot in good conscience watch a potential security risk play out no matter how funny the tweets are about this train wreck of an online launch, and they are hilarious. So, I am going to “imagine” a different future for tedcruz.org. Ted Cruz and any other candidate for president can still make some necessary adjustments and follow these very basic and essential must-dos before launching an online list-building and fundraising campaign:
1. Own your name online.
It’s a cheap upfront investment. Kind of like insurance for your online reputation. I hope Ted Cruz can appreciate the irony here.
Buy your domain names, like yesterday. Don’t wait for the news to leak to the media. Don’t wait to assemble a team of advisers or an exploratory committee. Don’t wait for your opponent to buy it or an enemy who is going to start trolling you.











